Inference Attack Resistant E Healthcare Cloud System with Fine Grained Access Control
Aim: to systematically construct a secure and privacy preserving e-health cloud system, so that it is immune to the inference attack and runs efficiently.
to protect the E-Healthcare data with fine-grained access control, the data can be either numerical or string value.
Proposed system: proposed two-layer encryption scheme
In the first-layer encryption, paper propose to define a specialized access policy for each data attribute in the EHR, generate a secret share or every distinct role attribute, and reconstruct the secret to encrypt each data attribute, which ensures a fine-grained access control, saves much encryption time, and conceals the frequency of role attributes occurring in the EHR.
In the second-layer encryption, paper propose to preserve the privacy of role attributes and access policies used in the first-layer encryption. Specifically, merge the first-layer access policies, add noise to the merged access policy, and encrypt the first-layer access policies under the noisy and merged access policy.
paper propose to let the cloud execute computationally intensive works on behalf of the data user without knowing any sensitive information. To preserve the access pattern (access frequency) of the data attributes in the EHR, we construct a blind data retrieving protocol.
Objectives:
• the first attempt to address the inference attack problem in the e-healthcare cloud system with fine-grained access control. Compared with the existing solutions, our scheme not only ensures novel functionalities, but also achieves higher efficiency on encryption, decryption, and role attribute revocation.
• systematically construct a two-layer encryption scheme. The first-layer encryption ensures the fine-grained access control, saves much encryption time, and conceals the frequency of role attributes occurring in the EHR. The second layer encryption enables the cloud to execute computationally intensive works on behalf of the data user, while preserving the privacy of access policies used in the first-layer encryption.
• design a blind data retrieving protocol, which preserves the access pattern of data attributes in the EHR and achieves high efficiency.
• provide rigorous security analyses and conduct extensive experiments to confirm the efficacy and efficiency of our proposed schemes.
Existing System: Drawback
1. only support the ‘black or white’ access control policy. Specifically, once a data user is authorized, he can access all the data attributes in the EHR.
2. suffer from the inference attack. The inference attack includes the frequency analysis attack, sorting attack, and cumulative attack. the most well-known attack is the frequency analysis attack, which breaks the classical encryption algorithms [14]. the inference attack is rooted in two aspects. 1) By observing the access frequency of the EHRs, the cloud can deduce the content of the EHRs with some background information even if they are encrypted. 2) Existing schemes adopt the conventional ciphertext policy attribute-based encryption to encrypt the EHR, which inevitably expose the access policy to the cloud. Therefore, the cloud can deduce sensitive data from the EHR with some background information.
3. must spend a large amount of time on secret generation for the repeated items.
System Architecture:
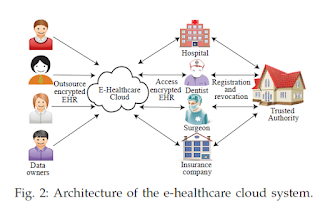
In proposed system four entities are involved, as shown in Fig. 2: they are the trusted authority, the data owners, the users, and the cloud.
The trusted authority is responsible for user registration and revocation. the trusted authority (TA) is responsible for distributing keys and parameters. TA is also responsible for distributing public parameters for the system.
· data owners are those who will outsource their EHR data to the cloud. To guarantee a fine-grained access control(Data owners should specify the access policy for each data attribute in the EHR, so that the data user can only access and decrypt his authorized data attribute.) while preserving data privacy, the data owners encrypt their EHR data before outsourcing. The fundamental reason
is that, once the sensitive EHR data are outsourced to the cloud, data owners would lose their control.
· To access this encrypted EHR data, the data user submits his role attributes to the cloud. Upon receiving the role attributes, the cloud retrieves the encrypted data and returns them to the data user. The data user further decrypts the ciphertexts and obtains the authorized data attributes in the EHR with his role attributes. Once the data user wants to retrieve data stored on the cloud, he submits his role attributes to the cloud, and the cloud will return the encrypted first-layer access policy. Upon receiving the ciphertext of the first-layer access policy, the data user performs the second-layer decryption, and retrieves his authorized data attributes from the cloud. With our design, the data retrieving process preserves the access pattern privacy. Finally, the data user conducts the first-layer decryption and obtains the authorized data attributes in the EHR with his role attributes.
· To improve the efficiency of the whole system, the cloud is expected to execute computationally intensive works on behalf of the data users. the cloud is not trusted, we treat it as ‘curious but honest’. the cloud can deduce sensitive data from the EHR with some background information.
Methodology:
at the beginning, the data owner conducts the first-layer encryption on each data attribute in the EHR with the attribute-based encryption algorithms. Then, to prevent the attacker from knowing the access policies used in the first-layer encryption, the data owner conceals these access policy, and conducts the second-layer encryption. After that, the data owner outsources the encrypted EHR data, the encrypted first-layer access policy, and the second-layer access policy to the cloud.
Distributing keys and parameters
the trusted authority (TA) is responsible or distributing keys and parameters.
First-layer Encryption
To achieve the fine-grained access control over the EHR data D, before outsoursing D to the cloud, the data owner first specifies a specialized role attribute set Aj , and a corresponding access policy Lj for each data attribute Dj in D, where j ∈ [1, d]. Then he encrypts D with the first-layer encryption.
Second-layer Encryption
To defend the cloud against knowing the actual role attributes and access policies, we propose to merge all the role attributes and access policies of data attributes in the EHR, add noise to the merged attributes and access policy, and encrypt the access policies used in the first-layer encryption under the noisy and merged access policy.
Returning Encrypted Access Policies
Upon receiving a data user’s access request, instead of returning all the data stored on the cloud and letting the data user decrypt a huge amount of EHR data, the cloud needs to filter out the EHR data that do not match the user’s role attributes, and only return the encrypted access policies that match the user’s role attributes.
Second-layer Decryption
When the user receives encrypted access policies computes the decryption key.
Retrieving Data with Access Pattern Privacy Preserved
To preserve the access frequency of a specific data attribute, we propose to design a blind data retrieving protocol.
First-layer Decryption
After obtaining the ciphertext the user first converts first layer access policies to public then user uses his secret key and parameters to decrypt the returned data attributes in the EHR.
Future Enhancement: Proposed system can be easily extended to support search functionality.
For additional details comment below with requirements.


Comments
Post a Comment